Burp proxy extensions
I’ve written some add-ons to Burp Proxy, by @portswigger.
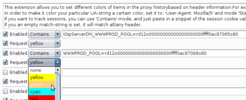
Proxy color
This is a little extension to color your proxy history based on characteristics in the HTTP headers. Very useful when doing multi-user testing scenarios, and you want to be able to distinguish between sessions (or browsers. ) This is how you set it up:
- Select if the inspection is to be on the request or response
- Three types of checks, either
-
Startswith- as it sounds, just checks if a header start matches exactly with what you’ve typed. Useful to e.g. flag server banners or funky headers. -
Contains- checks if the specified string is anywhere within the request. Useful for cookies, since may wind up in arbitrary order. -
Regexp- allows you to specify a more advanced string.
-
A few screenshots:
Referrer checker
Inspects the traffic, and looks for cross-domain include of scripts. Burps built-in checks for this is based on HTML-parsing (afaik), which does not give 100% coverage, obviously. My variant instead inspects the http-headers. My Firefox-based analysis shows the following observation:
| Requests to domains where referer domain differs from target | ||
|---|---|---|
| Referer | Accept-header | Cause |
| origin.com/foo/ | */* | Probably a script-tag |
| origin.com/foo/ | image/jpeg | Image tag |
| origin.com/foo/ | text/html | Frame/iframe tag |
| missing | */* | Manually entered by the user |
So, what the extension does, is simply check for Accept-header */* where target domain differs from referer domain, and flags a warning.
2013-02-22